Start using Cyber to power your prospecting.

Take control of your business' cyber health by building your Pillars of Cyber Hygiene. We live our lives and run our businesses in a digital world. Boot up your understanding of these simple and easy steps to be proactive in keeping your client data secure and your business running smoothly.
Cyber hygiene is the practice of simple and readily available techniques to proactively maintain the health and security of users, devices, networks, and data. Small businesses can leverage basic cyber hygiene pillars to form a strong foundation to protect their business’ cyber environment.
Small and Micro Businesses handle a lot of client data with a legal obligation for protection both in storage and transit. Protecting your business from data theft, ransomware, email phishing, and fraud is a daily challenge that requires a proactive approach. With cyber crime on the rise, hackers pick on Micro and Small Business as easy targets because they lack IT/Security resources and know-how. A recent studies by the Rogers Cybersecure Catalyst and the Business Development Bank of Canada (BDC) show almost 20% of Small Business suffered a cyberattack in 2021 and more than 1/3 Small Business lost over $100,000 from a cyber attack!
How can Micro and Small Businesses shield their systems and client data from the cyber risks? The answer to this is simple - get off the easy target list! Basic Cyber Hygiene can stop your business from being am easy victim. Hackers are predators of convenience. Build the Pillars of Cyber Hygiene and be proactive in defending your business from the onslaught of high frequency low effect cyber attacks.

Basic password hygiene is the founding Pillar of Cyber Hygiene. Micro and Small Businesses tend to overlook this vital cyber hygiene practice, whether personal employee passwords or passwords on workspace devices. If you reuse passwords for multiple accounts, sooner or later, one data breach will cascade through your accounts and you risk losing everything!Check to see if your passwords have been hacked now.
The main objective in password health is to have unique passwords for every account. This is far simpler than it sounds! Using Password Managers make having unique passwords a trivial task. Like digital wallets for all of your credentials, Password Managers can create randomized unique password for each of your accounts and integrate into Web Browsers, Mobile Apps, and Desktop Software so the whole process of password hygiene becomes a point and click affair.
How to make strong passwords:
Check out these Password Managers to boot up your password hygiene now:
Client data is vital for your Micro or Small Business as you use data to make essential decisions surrounding the everyday operations of the business and its long-time vision. Backing up and encryption your data is mandatory for any small business. Whether the data is private client information, sales numbers, human resources employee data, or pictures of your kids, you cannot risk losing any of it. Making backups ensures that you can recover lost data in the event of a data breach, theft, or lost/stolen computers.
Encryption is a standard practice for companies that handle client data in most jurisdictions. Data encryption ensures data even if a malicious actor steals your files, they cannot read the file content without a password to decrypt the file. Cyber Hygiene combo practice: encrypt your data with randomized and unique passwords stored in your Password Manager!
Check out these Backup & Encrypt techniques to boot up your cyber hygiene now:
Using a Firewall is a key cyber hygiene practice in this digital era, where almost all small business' operations take place online. A Firewall is a software or hardware tool that blocks malicious websites and threat actors from infiltrating users networks as they browse the internet.
Firewalls are simple plug & play devices that can intercept online traffic and execute network protection protocols, including:
A Firewall's content filtering and blocking capabilities protect Micro and Small Business computes, phones, and users from interacting with malicious actors, corrupted files, and suspicious sites.
Check out these Firewall solutions to boot up your cyber hygiene now:
Cyber hygiene for small businesses calls for installing effective anti-malware software that scans workspace devices, assesses threat exposure levels, prevents or minimizes current cyber-attacks, and averts future attacks. Small businesses must regularly update their anti-malware software and applications to cope with the rapidly changing threat landscape.
Fortunately for the Micro & Small Business owner, anti-malware and antivirus solutions are easily deployed, quick to install, and run in the background.
Check out these Anti-malware / Antivirus solutions to boot up your cyber hygiene now:
Just like a routine inspection of your car, Small Businesses must set baselines and track routine maintenance of their digital assets. Managing vulnerabilities is standard cyber hygiene practice and helps in staying on top of know cyber risks. Vulnerability Management may sound complicated and technical however with some simple tricks, this process can be as simple as point & click!
The objective of Vulnerability Management is keeping track of software patches and updates. If you can schedule a meeting, you can manage cyber vulnerabilities! Set a calendar reminder for your employees to check for Operating System Updates every week and reboot their computers every Friday night. This simple task will ensure automated updates are applied and low-grade malware is flushed from their systems.
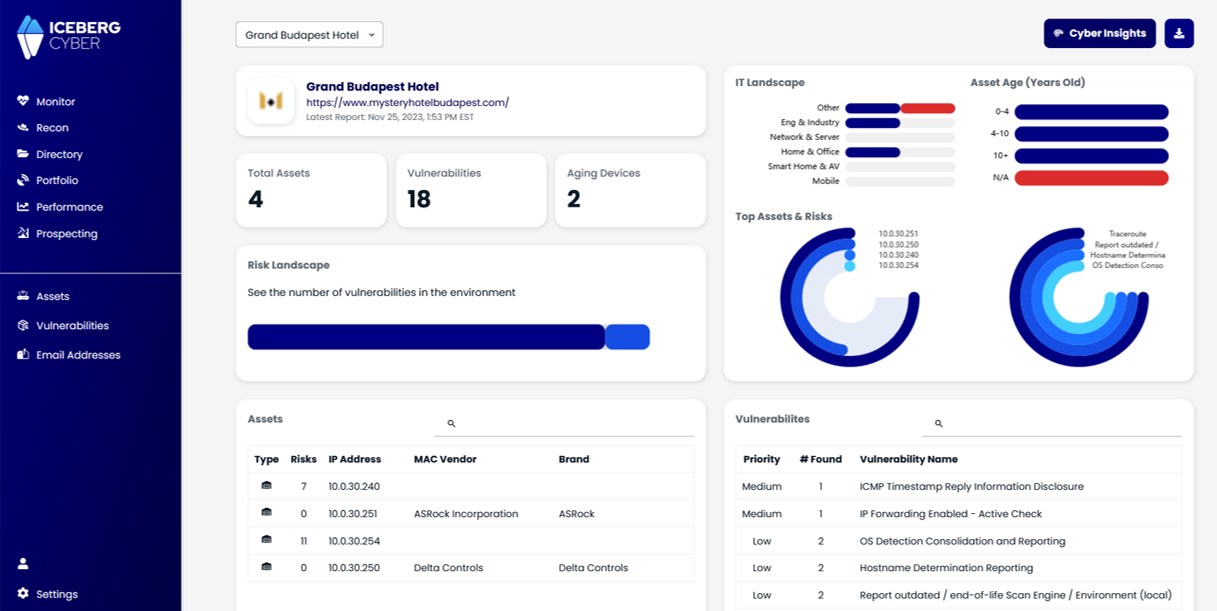
There are plenty of tools that can help you manage software versions, Known Exploitable Vulnerabilities, and cyber risks to your business. Don’t get lost in a forest of tools you don’t know how to use or tech jargon that flies over your head. Iceberg’s Cyber Briefs are the quickest and easiest way to build your Pillar of Cyber Hygiene! Cyber Briefs monitor your digital assets 24/7 and send you clear and simple monthly reports. We write our Briefs without the jargon! No tech IQ required. Forget about being lost with complicated terms and take control of your cyber risks. Cyber security made simple.
Boot up your Vulnerability Management solution with Iceberg’s Cyber Monitoring today!

Micro and Small Businesses are paying the price for lax cyber hygiene practices. With typical damages of over $100,000, data breaches, lost business, and lawsuits can be crippling to well intentioned Small Businesses. Take control of your cyber health and be proactive by building the 5 Pillars of Cyber Hygiene for your business. The Pillars are simple and accessible techniques that don’t require high tech IQ. Get off the easy target list and turn your Micro or Small Business into a Cyber Fortress!
For more information on how to disarm cyber threat actors, visit CISA Cyber Essentials and Cyber Secure Canada.




