Start using Cyber to power your prospecting.

The Federal Trade Commission (FTC) created the “Safeguards Rule” to ensure that businesses protect the security of customer information. The Safeguards Rule applies to non-banking financial institutions including mortgage brokers, accounting firms, credit unions, and more.
To comply with the Safeguards Rule, a business must implement a program that:
We live in a new world where cyber crime is a profitable business. Software automation and Artificial Intelligence (AI) has made it easy for hackers to attack small businesses at scale. Small businesses with lax security protocols are juicy targets for cyber criminals.

To further our point, here are a few cybersecurity statistics about small business in the past few years:
75% of SMBs could not continue operating if they were hit with ransomware. (Small Business Playbook)
The Safeguards Rule details nine elements that businesses must include in their IT security program.
Let’s take a look at the basic steps that businesses need to focus on:
1. Put someone in charge. This can be an employee or service provider. It’s your company’s responsibility to make sure that the Qualified Individual understands the security risks and can communicate them to the Board.
2. Conduct a cyber risk assessment. You can’t make an effective IT security program until you know what information you have and where it’s stored. Write your risk assessment down and include criteria for evaluating risks and threats. The Safeguards Rule requires you to assess employee accounts, data storage, network threats, and software vulnerabilities throughout your business. (We can do this for you at Iceberg Cyber!)
3. Regularly monitor and test the effectiveness of your safeguards. Test your procedures for detecting actual and attempted attacks. Implement continuous monitoring of your system to make sure you adapt with the changing threat landscape. Hackers adapt every day to make money by stealing from you. Stay one step ahead of them or face the consequences. Hackers only have to get lucky once.
4. Implement basic cyber hygiene. Encrypt your client data, put in place routine data backups, and use Multi-Factor Authentication for all accounts.These are simple steps that your Managed Service Provider can help you with. For more info, check out our blog post here.
5. Report to your Board of Directors. The FTC Safeguards Rule makes cybersecurity a key business concern for your Directors. They will be liable for negligence and non-compliance. What should the report address? Include an overall assessment of your business's compliance with its IT security program. Cover specific topics related to the program like the risk assessment, service provider arrangements, and recommendations for changes in the information security program. This is a team sport.
The updated Safeguards Rule has been in full effect since June of 2023. This means businesses need to begin working now to be ready in time. If your business does not have the internal bandwidth or resources to achieve compliance, you need to engage with an expert cybersecurity services provider
The FTC has a very broad definition of data as covered by the updated Safeguards Rule. This includes data provided directly by customers to obtain products or services, any data that is customer-related, and data resulting from or in conjunction with a transaction. Hardly any data are excluded
The new Rule requires regular reports to company boards including the overall status of the business's information security program, the business's current level of compliance with Safeguards Rule, the most recent risk assessment, any new management and control decisions, service provider arrangements, test results, information on security events or violations (and management’s responses thereto), and recommendations for changes
According to the FTC, penalties for non-compliance can be “extensive and expensive”. They take consumer privacy very seriously. Non-compliance consequences can include:

For many businesses in the United States, complying with the updated Safeguards Rule may seem like a daunting challenge.
Here are a few tips for how to get started:
IT Managed Service Providers (MSP) are experts in IT and cyber security. They can demystify the complex world of cyber crime and protect the assets most critical to your strategic business objectives and operations. Talk to the experts and don’t stand alone. Here at Iceberg Cyber, we are here to help. Simply get in touch with us to find out how we can make your business compliant.
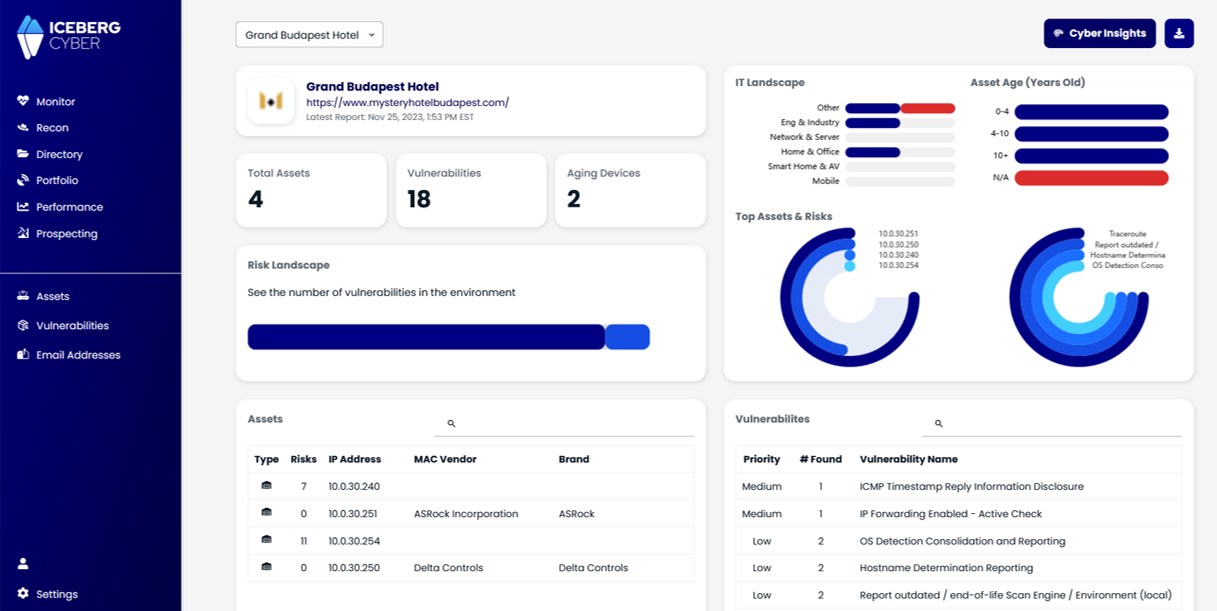
Get a cyber risk assessment and validate your current state, identify any existing gaps and vulnerabilities which are creating exposure to risk, and prioritize actionable recommendations based on ease of implementation and criticality to reduce risk quickly and effectively.
The risk assessment for your business, along with the risk assessment for the vendors you work with, are contingent upon a complete understanding and inventory of your assets, data and data flows.
For more information on the FTC Safeguards Rule:
https://www.ftc.gov/business-guidance/resources/ftc-safeguards-rule-what-your-business-needs-know




